
Websites use SSL certificates from trusted Certificate Authorities (CAs) to protect visitors’ sensitive information. These third-party entities verify a site’s or company’s identity before issuing the SSL cert. However, not all CAs are created equal, and some may not meet the high-security standards set by the website owner. Here’s where a CAA record comes into play.
This article covers the CAA record, from its definition to how it works. It also discusses how to add a CA record and why you’d want to set one up.
Table of Contents
- What is a CAA Record?
- CAA DNS Record Example
- How Does a CAA Record Work?
- How to Add a CAA Record?
- Why You Should Add a CAA Record in DNS?
What Is a CAA Record?
A CAA (Certificate Authority Authorization) record is a DNS record that allows a website owner to specify which Certificate Authorities (CAs) are authorized to issue SSL certificates for their domain.
The CAA record is a text record added to a website’s DNS zone file, and it contains one or more of the following pieces of information: issuer domain name, flag, and tag.
Adding a CAA DNS record is an additional security measure that improves the trustworthiness of SSL certificates by preventing unauthorized or fraudulent certificates from being issued.
CAA DNS Record Example
Here’s how a CAA record would look for SSL Dragon in a DNS server:
ssldragon.com . CAA 0 issue “digicert.com”
In this example, only DigiCert is authorized to issue digital certificates for this domain. Other certificate authorities must comply with this command or risk being distrusted. As the domain owner, you can decide how many CAs can issue SSL certs for your site and even specify the type of certificate.
Here’s an example of a CAA record for wildcard certificates:
ssldragon.com. CAA 0 issuewild “sectigo.com”
In this instance, only Sectigo can issue wildcard certificates for ssldragon.com. As per CA/Browser Forum Ballot 187, CAs must check CAA records before issuing an SSL certificate.
Now, that you know what a CA record is, it’s time to dive deep into its workings.
How Does a CAA Record Work?
Let’s take every element of a CAA record and break it down. We’ll use the same hypothetical example for the SSL Dragon website, and a real CAA record of Google.com. You can look it up yourself with the DNS checker tool.
ssldragon.com. CAA 0 issue “digicert.com”
The CAA record above includes the following parts:
- ssldragon.com – the domain you want to secure
- CAA – the record type
- 0 – flag
- issue – tag
- Digicert.com – the CA authorized to issue digital certificates for this particular domain.
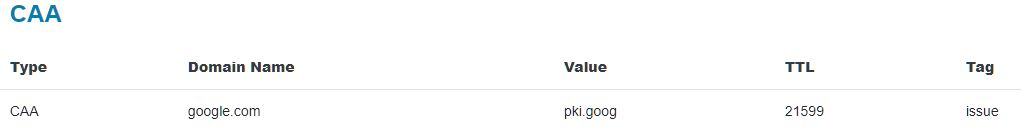
The Google example also contains the TTL attribute. We’re going to dissect the tags, flags, values, and TTL below:
Flags
A flag can be one of two specific states 1 (critical) or 0 (non-critical), with the latter being the default value.
- The 1 flag tells the CA that it can’t proceed with issuing the certificate if it doesn’t understand the property and should notify the domain owner via Email about the CAA record check failure.
- The 0 flag informs the CA that it can use any CAA record info in the DNS zone. If it doesn’t understand this record, it can use another in the DNS zone file.
Tags
A tag determines the action an authorized CA can perform when issuing digital certificates. The three tags that are defined in the proposed standard are issue, issuewild, and iodef. However, CAs can also create their custom tags to ease the certificate issuance process.
- The issue tag authorizes a particular CA to issue regular, non-wildcard certificates for the specified domain and all its subdomains.
- The issuewild tag authorizes a particular CA to issue wildcard certificates for the domain in question.
- The iodef (incident object description exchange format) tag notifies the domain owner via email when a certificate request fails the CAA check. Here’s how the syntax should look for the iodef property: ssldragon.com. CAA 0 iodef “mailto:[email protected]”.
TTL (time to live) is the period in seconds that a server should cache your CAA record.
How to Add a CAA Record?
Now that you know the elements of a CAA record, let’s create your own. With so many ways available how to create a CAA certificate record for your domain, we’ll focus on the two most common ones.
How to Add a CAA Record on Your DNS Server?
If you use your own DNS server, you can create your CAA record directly in the DNS BIND file.
- Use a text editor such as Notepad to open your domain’s DNS file.
- Add or update the DNS CAA record info in that file. Use the CAA record example we provided earlier. Include the flags, tags, value, etc.
- Save the zone file with your new configuration.
How to Add a CAA Record in cPanel?
If you want to add a CAA record via your hosting panel, here’s how to do it:
- Log into your cPanel account
- From the Domains section click on Zone Editor
- Next to the domain, you want to create a CAA record for click Manage
- In the Zone Editor page, find the Add Record button and expand it. From the drop-down list, select Add “CAA” Record
- Now you have to fill in the required fields:
- The name of the domain or subdomain you want to add a CAA record for
- The record type (CAA)
- The flag (0 or 1)
- The tag (issue, issuewild, iodef)
- The value (the domain name of the authorized CA)
- Click Add Record to finish your configuration.
Why You Should Add a CAA Record in DNS?
By now, you should be an expert on all things CAA records. But does your website need it?
Below we’ve listed a few reasons why you may consider setting up a CA record for your domain:
- Improved Website Security. By limiting the number of CAs that can issue certificates for your domain, you reduce the risk of a malicious attacker obtaining a fraudulent certificate for your website.
- Compliance with Industry Standards. Setting up CAA DNS records is part of industry best practices. The CA/Browser Forum and PCI Security Standards Council recommend adding DNS CA records and thinking of mandating them to tighten web security threats.
- Operational Risks Reduction. By specifying which CAs are authorized to issue certificates for your domain, you can reduce the risk of operational mistakes and misconfigurations that could lead to security breaches or website downtime.
- Faster SSL Validation. CAA records can reduce the SSL validation time. When a CA receives a certificate request for a domain, it must check if a CAA resource record exists and if the requested CA is authorized to issue certificates for that domain. Providing this information ahead of time can speed up the validation process.
- Brand Protection. CAA records can protect your brand reputation by preventing fraudulent certificate issuance and blocking phishing attacks or other malicious activities that could damage your brand reputation.
Final Thoughts
SSL certificates are now an essential element of every website. And while breaking the HTTPS encryption is beyond human capabilities, cyber-attackers are always searching for clever ways to compromise your name.
Thankfully, CAA records are another excellent security measure to protect your brand identity. CAA records give you full control over the certificate issuance process.
Save 10% on SSL Certificates when ordering today!
Fast issuance, strong encryption, 99.99% browser trust, dedicated support, and 25-day money-back guarantee. Coupon code: SAVE10



























