
At first glance, an SSL certificate seems straightforward. You install it on your server to secure your visitors’ sensitive data, and it works flawlessly until expiration. Most web owners rarely delve deeper into SSL/TLS technical aspects.
They let professionals handle the certificate configuration and renewal. Many won’t even care about the difference between root certificates and intermediate certificates, but if you want to install your cert by yourself, you should know the mechanism behind it.
Table of Contents
- Root, Intermediate, and Server Certificates
- Root Programs and Root Stores
- Public Key Infrastructure
- Digital Signatures
- What Is the SSL Chain of Trust?
- What Is a Root SSL Certificate?
- What is an Intermediate SSL Certificate?
- What is a Server SSL Certificate?
- What Is the Difference Between a Root and an Intermediate Certificate?
- How to Tell if a Certificate is Root or Intermediate?
Root, Intermediate, and Server Certificates
Users without prior experience who prefer to install an SSL certificate by themselves are in for a surprise. The moment they open the ZIP archive folder that the CA (Certificate Authority) sent via email, they discover not one, but a couple of SSL files.
One is the server certificate issued for your domain; the other is the intermediate certificate, and finally, there’s also the root certificate. The intermediate certificate links your server certificate to the root certificate. Altogether, they form the SSL chain of trust. If one component in the chain is missing, browsers won’t trust the server’s SSL certificate and will issue an HTTPS warning.
Wait, what? Server certificates, intermediate certificates, root certificates, chain of trust, it’s all a bit too much for novices. If you’re one of them don’t worry, in this article, we’ll explain the difference between root certificates and intermediate certificates and why they are crucial to how the SSL/TLS works. But first, a few words about the structure that holds them all together.
Root Programs and Root Stores
The root certificate is a crucial element of the entire SSL/TLS architecture, as it validates the end-user certificate and keeps everything in place. Hacking a root cert is the worst-case scenario, as it compromises all its intermediate and server certificates.
To manage root certificates and their public keys more efficiently and securely, the leading technology companies have developed root programs that, besides following strict guidelines and regulations, include a root store.
The root store includes pre-downloaded root certificates (and their public keys) that stay on the device’s operating system or third-party software such as web browsers. Here are a few examples of popular root programs.
- Apple
- Mozilla
- Microsoft
While not all root programs require identical compliance, they adhere strictly to the CA/B forum’s baseline requirements.
Public Key Infrastructure
Public Key Infrastructure, or PKI, is the foundation of the SSL industry, as it executes the intricate processes behind certificate issuance and user validation. Public and private keys work together to encrypt and decrypt sensitive data over a network.
The SSL certificates contain the public key, while the origin server has the private key. When browsers try to connect to servers, the SSL handshake uses public key cryptography to identify the origin server and exchange data. If the site’s SSL certificate is not valid, the connection will not be secure. Learn more about SSL certificates and how they work.
Digital Signatures
Digital signatures are advanced electronic signatures that require identity verification via a key or certificate associated with them. In the context of SSL, think of them as digital certification.
As you will see in the SSL chain of trust diagram, a root certificate digitally signs an intermediate cert and passes some of its trust to the intermediate SSL. The latter is automatically trusted because the signature comes directly from the root.
A Browser uses the public key to verify digital signatures and authenticate the server (end-user) certificate. It checks on every certificate within the SSL chain of trust up until the final root cert that comes pre-installed in the browser root store. If the browser can identify all the chain certificates, it won’t trust your SSL certificate.
What Is the SSL Chain of Trust?
Let’s come back to the chain of trust and look at the whole picture. The SSL chain of trust is an ordered list of certificates that allow the receiver (a web browser) to verify that the sender (your secure server) and the CA are reliable.
The image below illustrates how the chain of trust functions:
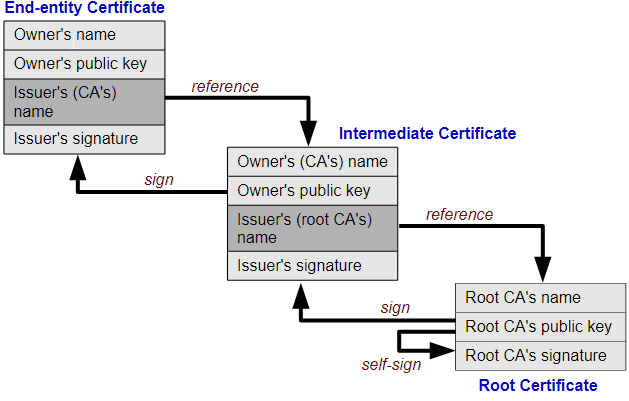
Image credit: Yanpas – CC BY-SA 4.0
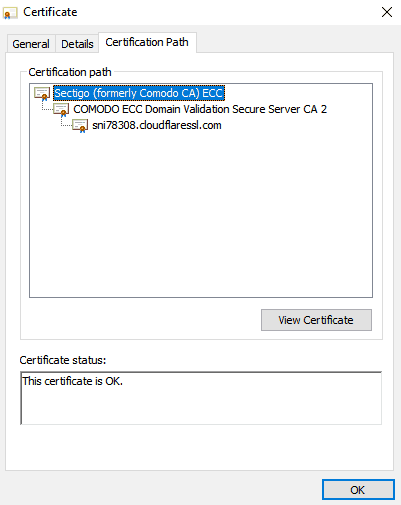
You can also inspect the SSL chain trust by clicking the padlock of any website and selecting the Certification Path tab. If you look at SSL Dragon’s Certification path, you’ll see from top to bottom, the root certificate, intermediate certificate, and server certificate (SSL Dragon uses a Cloudflare SSL certificate as part of CDN service).
Now that you know about the chain of trust, let’s take each element and put it under the microscope.
What Is a Root SSL Certificate?
A root SSL certificate sits at the top of the trust hierarchy and is the backbone of Public Key Infrastructure. Root SSL certificates are signed by trusted Certificate Authorities. Who decides which CA is trustworthy? In a nutshell, browsers, and applications because they include a root store in their installation pack.
A root store is a list of pre-downloaded, trusted root certificates from various CAs. For instance, if the CA root certificate isn’t included in Google’s root store, Chrome will flag the website using said CA as not secure. You can read more about Certificate Authorities and who regulates them.
A root certificate is used to issue other certificates. If the private root keys were stolen, cyber-criminals would forge their own trusted certificates. As a result, all the existing certificates signed by the hacked CA would have to be revoked. If something goes wrong with the root certificate, the CA is swiftly removed from all the root stores and ceases to exist.
To avoid the unthinkable, CAs use rigorous security procedures. They store the CA key in a unique Hardware Security Module. Moreover, the physical computing device resides in a locked vault with steel doors and guards.
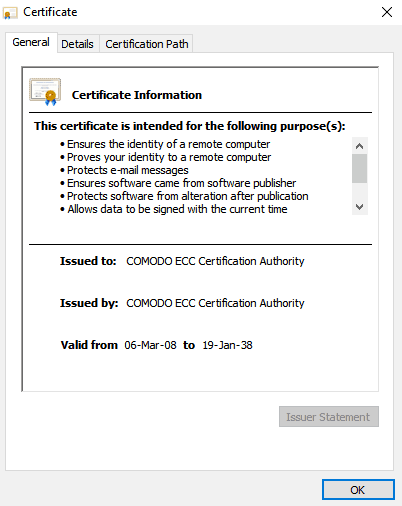
Unlike commercial certificates, root certs have a much longer lifespan. Here’s the validity period of Sectigo (formerly Comodo CA) ECC. As you can see it expires in the distant 2038.
What is an Intermediate SSL Certificate?
Issuing an SSL Certificate to the end user directly from the root certificate is too dangerous. To further protect themselves the CAs, came up with another layer of security – the intermediate certificate.
The root CA signs the intermediate root with its private key, and in turn, the intermediate CA uses its private key to issue SSL certificates to the general public. The intermediate certificate or certificates (some CAs use several intermediate certs between the root and end-user certificate) act as a link of trust.
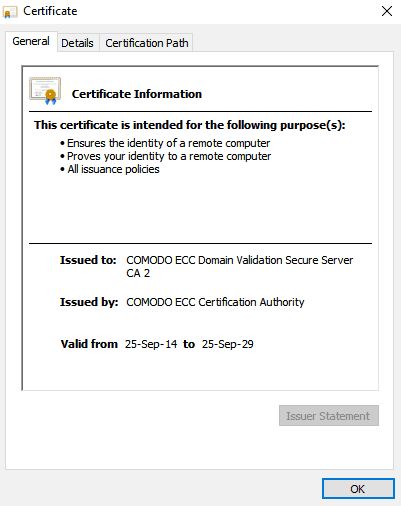
Browsers need them to identify the root CA and accept the server certificate. That’s why your SSL installation folder may contain an intermediate certificate, along with your primary cert. Intermediate certificates also have longer validity than end-user SSL certificates, although it’s shorter than the validity of a root certificate.
What is a Server SSL Certificate?
A server SSL certificate, also called a primary SSL certificate or an end-user certificate, is issued by a certificate authority to your domain name. It verifies domain ownership and, depending on the validation level, a company’s legal status.
Server certificates are signed from intermediate certs, which come from the root certificates. Server SSL certificates have a one-year validity and are the certificates everyone gets when ordering SSL.
To encrypt your website and activate HTTPS, you must install an SSL certificate on your server. Hence the name – server SSL certificates.
What Is the Difference Between a Root and an Intermediate Certificate?
The root vs. intermediate certificate comparison comes down to their hierarchical position in the chain of trust. Without root certificates or root CAs, there won’t be intermediate certs or server certificates.
Here’s what sets root certificates and intermediate certificates apart:
1. Their Overall Value
Root certificates are the core of the entire SSL issuing process. If a root cert gets compromised, the breach could bankrupt the CA that issued it. On the other hand, intermediate certificates, while also important, are, ultimately, just intermediates and hold a lesser weight in the chain of trust.
2. Digital signature sequence
The root certificate uses the private key to sign the intermediate certificate, while the latter uses the same key to sign other intermediates and the server certificate.
3. Issuance procedure
The Certificate Authority signs the root certificate, which is then included in the root stores of various apps and programs. To better protect their root certs, CAs use intermediate certificates to act as the “middlemen ” between root and server certificates.
4. Lifespan
Root certificates last up to 10 to 20 years, while intermediate certs have a shorter validity due to security reasons. As you move through the chain of trust, the SSL validity diminishes, with end-user certs having just a one-year lifespan.
5. Storage Protocol
Root certs reside in a bulletproof hardware security module, behind still doors, and under 24/7 guard supervision. As for the intermediate certs, they are stored on your server in the installation directory.
How to Tell if a Certificate is Root or Intermediate?
You can tell a root certificate from an intermediate one by inspecting the certificate itself. If the Issued to and Issued by fields are identical, then it’s a root certificate, as only a valid certificate authority can issue trusted roots; otherwise, it’s an intermediate.
Another way to differentiate them would be to check the Certification Path. The certification, which appears at the top of the list, is the root certificate, followed by the intermediate and server certs. As we’ve already mentioned, root certificates have the longest validity, so you can also look at the dates when comparing root and intermediate certificates
Final Words
Hopefully, you now have a complete grasp of what really makes a digital certificate so secure. By understanding what is the difference between root certificates and intermediate certificates, you’ve solved the SSL/TLS puzzle. The SSL chain of trust is one of the reasons why SSL certificates are ubiquitous and efficient. The other is the high-end encryption impossible to crack by even the brightest hacker.
Frequently Asked Questions
When you order an SSL certificate, the CA delivers the installation files in an archived ZIP folder. Inside it, you will find the server certificate issued for your domain and a CA Bundle file containing the root and intermediate certificates. Some CAs may send the root and intermediate certificates in separate text files
Copy Link
You don’t need to identify the root and intermediate certificates when configuring your SSL certificate if you’ve received them inside a CA Bundle file. Open the file with any text editor, and you’ll notice that all certificates are inside in the correct order. If you’ve received the root and intermediate certificates in separate files, check the file name, as it must include the word “root” or “intermediate” for easy identification.
Copy Link
To combine the root and intermediate certificates, you need to chain all of them (excluding the server certificate) in the order of verification. The quickest way is to copy the contents of your root certificate and paste them below the intermediate certificates. The combined file will have the following order:
- Intermediate certificate 1
- Intermediate certificate 2
- Root Certificate to complete the chain of trust.
Copy Link
If a root certificate is missing, the solution is to download the trusted root CA first and then attempt to install the certificate again. To fix the intermediate certificate missing error, ensure you have followed all the SSL installation steps required for your server, including uploading the intermediate certificates in the correct order and file format.
Copy Link
Save 10% on SSL Certificates when ordering today!
Fast issuance, strong encryption, 99.99% browser trust, dedicated support, and 25-day money-back guarantee. Coupon code: SAVE10



























