
Welcome to the essential guide on Certificate Revocation Lists (CRLs), a critical aspect of online security. This guide will cut through the jargon and get straight to the point.
Have you ever wondered what happens when a digital certificate becomes untrustworthy? Think of it as a red flag in the digital world, signaling potential risks. We’re here to break down CRLs — what they are, what they contain, and why you should care.
We’ll provide real examples of revoked certificates, showing you the tangible consequences of overlooking their importance. By the end of this guide, you’ll grasp the significance of regular CRL checks in maintaining the integrity of digital certificates.
No frills, just facts. Let’s dive straight into it. So, what is CRL in cyber security?
Table of Contents
- What Is a Certificate Revocation List?
- What Is the Purpose of Certificate Revocation Lists?
- What Does a CRL Include?
- How Does CRL Work?
- How to View the Certificate’s Revocation Status
What Is a Certificate Revocation List?
A Certificate Revocation List, or CRL, is essentially a blacklist of discredited digital certificates. Maintained by a Certificate Authority (CA), this list contains all SSL certificates the CA has revoked before their scheduled expiration dates. This process is also known as PKI certificate revocation.
When you’re browsing online, your browser is constantly cross-checking this list. If it encounters a certificate on the CRL, it won’t trust the website or service associated with that certificate. It’s an essential security measure that helps ensure the integrity of data transmission online.
But why would CAs revoke a certificate in the first place? There could be multiple reasons. Perhaps the certificate’s private key was compromised, or the CA issued the certificate in error. Regardless of the reason, once a certificate is on the CRL, it’s no longer trusted.
To ensure the effectiveness of this security measure, CAs must regularly update the CRL and make it easily accessible to users’ systems. It’s one of the chief responsibilities of the Certification Authority. They must also provide a mechanism for users to check the revocation status of certificates, typically through an online service.
What Is the Purpose of Certificate Revocation Lists?
CRL is a tool that enhances online security by managing and keeping track of insecure certificates that could compromise a system’s safety. Its purpose is to provide a strict check and balance system, flagging any questionable certificates to prevent potential cyber-attacks.
By understanding the role of the CRL, you can better manage your digital security framework. Here are a few key points to note:
- CRLs contain certificates that are no longer valid.
- Regular updates of the CRL are necessary to keep track of invalid certificates.
- The use of CRLs reduces the risk of certificate misuse.
- Ensuring SSL certificate validity through CRLs is a proactive security measure.
Benefits of CRL
CRL offers several key benefits:
- It prevents unauthorized access by immediately invalidating compromised certificates.
- It supports the online certificate status protocol (OCSP), which verifies the status of a digital certificate.
- It enhances overall cybersecurity by maintaining certificate integrity.
- It mitigates potential cyber risks associated with compromised or expired certificates.
- It ensures a secure and reliable online environment, promoting trust.
Managing Insecure Certificates
While bolstering your online security, it’s crucial to understand the purpose of the CRL in managing insecure certificates.
As you already know, a CRL is a list of revoked public key certificates by the issuing Certificate Authority before expiration. These certificates, known as untrusted certificates, are invalidated for various reasons, such as compromise of the private key or if they’ve been fraudulently signed. They pose a significant risk to your online security.
Hence, the CRL plays an integral role in reducing this risk. It facilitates the rapid identification and rejection of untrusted certificates, preventing third-party access and potential data breaches.
What Does a CRL Include?
A CRL includes vital elements such as the Certificate Authority’s name, the list’s update time, and a list of revoked certificates, each with its own unique serial number and revocation date.
- Version Number: Indicates the version of the CRL format.
- Signature Algorithm Identifier: Specifies the algorithm used by the CA to sign the CRL.
- Issuer: Identifies the entity (usually a Certificate Authority) that issued the CRL.
- This Update: Indicates the issuance date of the CRL.
- Next Update: Specifies when the next CRL is scheduled to be issued. Until this date, the current CRL is considered valid.
- Revoked Certificates: Contains a list of digital certificates that the CA has revoked. Each entry includes the serial number, the revocation date, and sometimes a reason code.
- Extensions: Additional information or features, such as CRL distribution point, authority key identifier, or other custom extensions.
CRL is periodically updated and distributed by the CA to ensure that relying parties (entities using the certificates) can access the latest information about certificates revoked within a timeframe.
How Does CRL Work?
Now, let’s see how CRL operates. The CRLs are distributed to specified points, followed by meticulous revocation checking. Handling revoked certificates and regularly updating the CRL are crucial steps to ensure the system’s effectiveness and security.
CRL Distribution Points
The CRL distribution points are a central part of how CRLs function. They are servers that store and distribute CRLs. They act as a hub for managing and verifying the status of digital certificates.
The distribution point receives updates from the CA regarding the revocation status of certificates. Each time a certificate is revoked, the CA updates the CRL distribution point.
End entities, such as browsers, can query the CRL distribution point to check the revocation status of a certificate. The distribution point transmits the CRL to all entities that request it.
Revocation Checking Process
While keeping an eye on the role of CRL distribution points, let’s delve into how the revocation checking process, or the functioning of the CRL, actually works.
During the certificate revocation check process, the system first fetches the CRL from a specified distribution point. This list contains all the certificates that have been revoked before their expiration dates.
Your system then cross-checks the presented certificate against this list. If the certificate is found in the CRL, it’s deemed untrustworthy and the connection is rejected. This process ensures that revoked certificates aren’t mistakenly trusted, maintaining security.
However, it’s crucial that the CRL is kept up-to-date, as outdated information can compromise the check process’s integrity.
Handling Revoked Certificates
Here’s how the CRL process works:
- The CA issues certificates and also maintains the CRL.
- If a certificate is compromised, the CA revokes it.
- The CA updates the CRL to include the Serial Number of revoked certificates.
- When a server receives a client’s certificate, it checks the CRL.
- The server rejects the connection if the client’s certificate is on the CRL.
Updating CRL Regularly
The CRL issuer periodically issues updates to maintain the integrity and reliability of the list. This regular updating eliminates the risk of outdated information, which could compromise the security of your system and sensitive data.
Updating isn’t a mere manual task. Instead, it involves a complex, technical process dictated by specific protocols. When a CA revokes a certificate, it updates the CRL. Then, the CRL is digitally signed by the issuer and distributed to all entities that rely on it. This process must run correctly, as errors can lead to significant security vulnerabilities.
How to View the Certificate’s Revocation Status
Accessing a CRL depends on the specific Certificate Authority that issued the certificates you are interested in. CRLs are typically made available by CAs at specific distribution points, as specified in the certificates.
To find the CRL distribution point, you can inspect the certificate itself. Here’s a general guide for certificate revocation status checks:
Via the Certificate Details in Your Browser
If you have the certificate file, you can usually open it using a certificate viewer or an application that supports certificate inspection.
- Click on the padlock icon next to the URL.
- Click on Connection is secure then on Certificate is valid.
- Look for the CRL Distribution Points (CDP) extension.
- The CDP extension contains one or more URLs pointing to the locations where the CRLs are published.
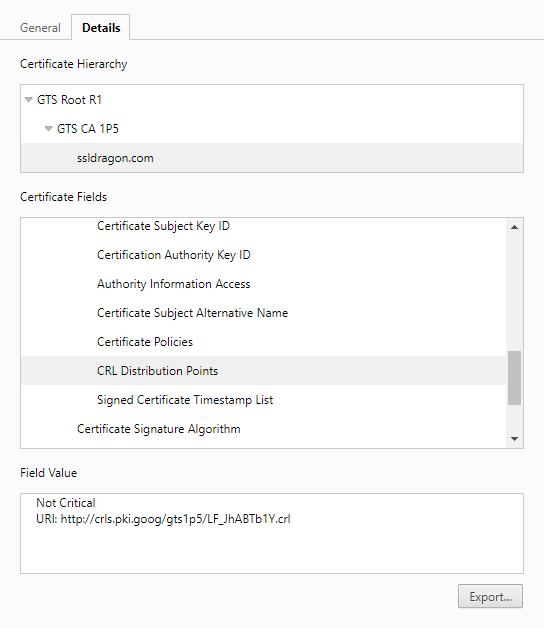
- Open the Details tab, and, under the Certificate Fields scroll down to Extension.
- Click on the CRL Distribution Points.
- In the Field Value, copy the URL and paste it into the address bar.
- The browser will download the CRL file. Open it to see the revocation list information.
Via OpenSSL
Here’s an example of how you might use OpenSSL to retrieve a CRL:
openssl crl -inform DER -in exampleca.crl -text
Replace exampleca.crl with the actual filename or URL of the CRL you want to inspect.
Keep in mind that some CAs might provide CRLs through different mechanisms, such as LDAP (Lightweight Directory Access Protocol) or other protocols. Additionally, some CAs may offer OCSP (Online Certificate Status Protocol) services as an alternative to CRLs.
If you’re working with a specific CA, check their documentation or website for information on how to access their CRL files. If you’re just looking for examples, some CAs provide sample or publicly available CRLs for testing purposes, but be cautious and respect any terms of use associated with such resources.
FAQ
Where Do I Find the Certificate Revocation List?
To run a certificate check, the client connects to the Certificate Authority’s specified URLs to download Certificate Revocation Lists. These lists contain information about revoked certificates. You can find the CRL URLs in the SSL Certificate’s Details under Certificate Extensions, specifically in the CRL Distribution Points section.
How Do I Create a Certificate Revocation List?
To create a CRL, use a CA tool or software to generate the list, including details of revoked certificates, and then distribute the CRL to entities relying on it for certificate validation in a Public Key Infrastructure (PKI) system.
How Do I View the Certificate Revocation List in Windows?
In Windows, you can view the Certificate Revocation List (CRL) by opening the Certificate Manager through the “certmgr.msc” command, navigating to the “Revocation Lists” folder, and then selecting the desired CRL to view its details. Alternatively, you can use the “certutil” command in the Command Prompt with the “-urlcache” option followed by the CRL URL to display information about the CRL.
What is The Difference Between CRL and OCSP?
Both methods are used in cybersecurity to check whether a digital certificate, like those used in HTTPS, is still valid. The main difference is in how they provide this information: CRL uses a periodically updated list of revoked certificates, while OCSP directly queries a certificate authority in real time to confirm a certificate’s status.
Who is checking the Certificate Revocation Status?
The responsibility for checking the certificate revocation status falls on the client (browser). It’s the browser’s duty to verify whether a certificate has been revoked before establishing a connection.
What Happens to a Revoked Certificate?
When a certificate is revoked, it signifies that it is no longer deemed valid. Relying parties, such as browsers, will consequently reject connections based on that certificate, enhancing security and mitigating potential risks.
Conclusion
In conclusion, a Certificate Revocation List helps maintain digital communication security by promptly invalidating compromised or revoked certificates. Its effective implementation ensures the integrity and trustworthiness of online transactions and communication. As technology evolves, continual refinement of CRL in cyber security mechanisms remains imperative to keep digital security frameworks robust.
Save 10% on SSL Certificates when ordering today!
Fast issuance, strong encryption, 99.99% browser trust, dedicated support, and 25-day money-back guarantee. Coupon code: SAVE10



























