
Are you facing frustrating HSTS errors on Chrome or Firefox? Don’t despair! This detailed guide is designed expressly for you.
We’ll walk you through what it is, why you’re encountering errors, and most importantly, how to disable HSTS in Chrome and Firefox.
With our concise steps and clear explanations, you’ll fix this technical error in no time. Let’s begin!
Table of Contents
- What Is HSTS?
- What Is the HSTS Error?
- How to Disable HSTS in Chrome Browser?
- How to Disable HSTS in Firefox Browser?
What Is HSTS?
HSTS stands for HTTP Strict Transport Security, a web security policy mechanism that helps to protect websites against man-in-the-middle attacks such as protocol downgrade attacks and cookie hijacking. HSTS ensures that a web browser communicates with a website only over secure, encrypted connections. It’s one of the most efficient online security measures against sensitive data theft.
How Does HSTS Work?
HSTS implementation involves configuring the web server to include the HSTS header in HTTP responses. This header, known as “Strict-Transport-Security,” specifies the maximum time (in seconds) for which the browser should enforce HTTPS, referred to as “max-age.”
Optionally, the header may incorporate directives like “includeSubDomains,” extending the HSTS policy to all subdomains, and “preload,” signaling browsers to include the domain in their HSTS preload lists. Being on the preload list ensures HSTS enforcement even on the initial visit.
Upon a user’s visit to an HSTS-enabled site, the browser recognizes the HSTS header and internally stores this information. Enforcement is automatic during subsequent visits within the specified “max-age” duration.
Even if a user attempts to access the site via “http://” or clicks on an HTTP link, the browser seamlessly converts the request to HTTPS before transmission.
Throughout the HSTS policy duration, the browser consistently uses HTTPS for all subsequent requests to the HSTS-enabled domain, disregarding any attempts to access the site over an unencrypted connection.
HSTS Examples
Here are a few examples of HTTP Strict Transport Security headers:
Basic HSTS Header
Strict-Transport-Security: max-age=31536000
In this example, the max-age directive is set to 31536000 seconds (1 year), indicating that the browser should enforce the HSTS policy for that duration.
HSTS with Subdomain Inclusion
Strict-Transport-Security: max-age=31536000; includeSubDomains
This example includes the includeSubDomains directive, indicating that the HSTS policy should apply to all subdomains of the current domain.
HSTS Preload
Strict-Transport-Security: max-age=31536000; includeSubDomains; preload
This example includes the preload directive, signaling to browsers that the domain should be included in their HSTS preload lists. Being on the preload list means that HSTS is enforced even for the very first visit to the website.
HSTS with Custom Subdomain Max-Age
Strict-Transport-Security: max-age=31536000; max-age=2592000; includeSubDomains
In this example, the main domain has a max-age of 1 year, while the subdomains have a shorter max- age of 30 days.
Web admins should configure HSTS headers to fit their security needs and domain structure. Test and monitor regularly for optimal effectiveness. Now, let’s explore some HSTS benefits and limitations.
HSTS Benefits
A proper HSTS configuration provides these key benefits:
- Mitigation of Man-in-the-Middle Attacks: HSTS prevents eavesdropping and data tampering by thwarting potential cyber-attacks.
- Protection Against Session Hijacking: HSTS protects against session vulnerabilities by ensuring secure transmission of session cookies.
- Protocol Downgrade Prevention: It reduces the threat of attacks leveraging insecure communication protocols.
- Enhanced User Privacy: Boosts user privacy by securely transmitting sensitive information, improving trust in the website.
- Prevention of SSL Stripping Attacks: Ensures users’ interactions with the website remain encrypted and secure, minimizing the risk of successful SSL strip attacks.
HSTS Limitations
As with any technology, HSTS settings have some limitations. Here are a few of them:
- Dependent on Browser Support: HSTS deployment and effectiveness rely on browser support, and users employing unsupported or outdated IE browsers may not benefit from its security features.
- Strict Policy Persistence: Once you implement HSTS, the policy is persistent for a specified duration, making it challenging to revoke or modify if needed quickly.
- Potential for Expired Certificates: If a website’s SSL/TLS certificate expires, users may face difficulties accessing the site until the certificate is renewed, even if HSTS is in place.
Next, let’s turn our attention to the HSTS error. But, before diving into how to disable HSTS in Chrome and Firefox, let’s first understand what the HSTS error is and why it occurs.
What Is the HSTS Error?
The HSTS error occurs when a site that should load over HTTPS secure connections loads over HTTP (insecure connections). As a result, web browsers like Chrome or Firefox will display an HSTS error, blocking the user from accessing the website. The site’s HSTS policy, which instructs browsers to only connect via secure connections, triggers this error.
What Causes the HSTS Error?
When a user encounters an HSTS error, the browser typically displays a warning or error message, preventing the user from accessing the website. Troubleshooting HSTS errors involves addressing the specific issues causing them, such as updating SSL certificates, fixing mixed content issues, or ensuring the correct server time.
Common HSTS errors include:
- Certificate Issues: If there is a problem with the SSL/TLS certificate of the website, such as an expired or invalid certificate, it can trigger an HSTS error.
- Invalid HSTS Policy: If the website sends an invalid or improperly formatted HSTS policy, browsers may reject the connection.
- Mixed Content: If the website contains a mix of secure (HTTPS) and non-secure (HTTP) content, it can trigger HSTS errors.
- Clock Difference: HSTS relies on the correct system time on both the client (user’s computer) and the server. If there’s a significant time disparity, it can cause HSTS errors.
How to Disable HSTS in Chrome Browser?
Disabling HSTS in Chrome involves a specific set of steps. HTTP Strict Transport Security protects sensitive data by forcing secure https connections. But sometimes, you may need to disable HSTS due the “You cannot visit domain.com right now because the website uses HSTS.” error or other https issues.
To disable HSTS, you need to clear HSTS settings in Chrome.
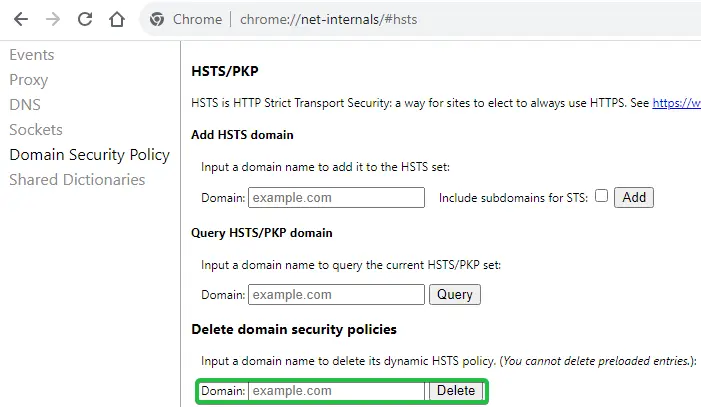
- Type chrome://net-internals/#hsts into the address bar to access Chrome HSTS settings.
- Look for the Delete domain security policies section under the HSTS menu. Type the domain name where you’re experiencing the HSTS error in the Domain field and click on the Delete button to remove the HSTS settings for that site.
If the error persists, you can modify the local HSTS settings through the registry editor on Windows OS:
- Right-click Start, then select Run. Type regedit in the Open: box, and then select OK.
- Navigate to HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Google\Chrome.
- In the right-hand side of the window, look for the HstsEnabled value. If it’s not there, create it by right-clicking on the empty space, selecting New > DWORD (32-bit) Value, and naming it HstsEnabled.
- Double-click on the newly created value and enter 0 in the Value data box to disable HSTS.
Remember, disabling HSTS can expose sensitive data to potential threats. Therefore, only use this method when the HSTS Chrome error disrupts your browsing, and enable it once you’ve fixed the connection issues.
Alternative Method: Using Chrome DevTools:
- Open Chrome and navigate to the website where you want to disable HSTS.
- Open the Chrome DevTools by right-clicking on the page, selecting Inspect, and then going to the Network tab.
- Reload the page (you can use Ctrl + R or Command + R).
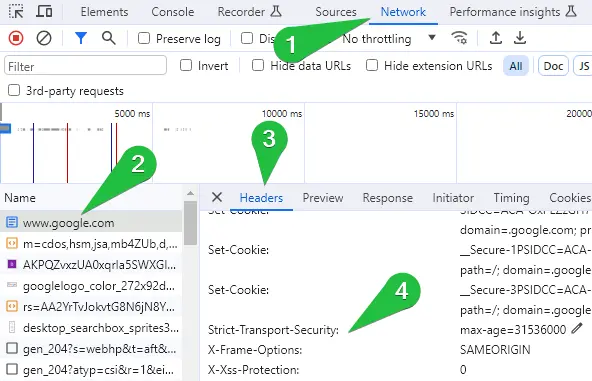
- Look for the initial request (the first request made when you reload the page). It should be the HTML document.
- In the Headers section of the request, look for the Strict-Transport-Security header.
- You can modify the max-age value to 0 or remove the entire header. This will instruct Chrome not to enforce HSTS for the specified domain.
How to Disable HSTS in Firefox Browser?
You can disable HSTS settings in Firefox for a specific site by following these steps:
- Type about:config in the address bar and press Enter.
- Accept the risk and continue.
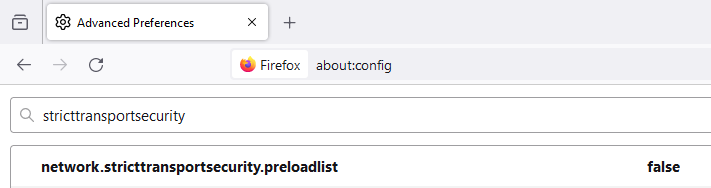
- In the search bar, type stricttransportsecurity.
- You should see an entry named network.stricttransportsecurity.preloadlist. Double-click on it to toggle the value to false. This disables HSTS.
Remember, clearing HSTS will delete HSTS settings for all websites, not just the one you’re having trouble with. Now that you’ve taken these steps, you’ll need to restart Mozilla Firefox for the changes to take effect.
If you don’t see the changes after restarting Firefox, you might need to clear the cached data. To do this, go to the Edit Menu, select Preferences, click Privacy & Security, then click the Clear Data button. Ensure to check Cached Web Content and hit the Delete button. After you clear the HSTS cache, restart Firefox again.
FAQ
Is HSTS Still Used?
Yes, HSTS is still used as a website security mechanism to enforce the use of secure connections over HTTPS by web browsers and protect all the data in transit.
Do All Browsers Support HSTS?
Yes, most modern web browsers, including Chrome, Firefox, Safari, Edge, and others, support HSTS ) However, it’s always advisable to check the specific documentation of each browser for the most up-to-date information.
Is HSTS Enabled by Default?
HSTS is not enabled by default on all websites. Website administrators must configure their servers to include the HSTS header in the response, specifying the duration for which HSTS should be enforced. Once a browser encounters the HSTS header, it will remember to enforce secure connections for the specified duration.
Do I Need to Enable HSTS?
We recommend implementing HSTS to enhance security by ensuring that all communications with the server occur over a secure HTTPS connection. However, it’s not mandatory, and the decision to enable HSTS depends on the specific security requirements and considerations.
What Are the Risks of Not Having HSTS?
Without HSTS, there is a risk of man-in-the-middle attacks where an attacker could potentially intercept and manipulate unsecured connections. HSTS helps mitigate this risk by enforcing HTTPS and protecting users from certain types of security threats.
Should I clear HSTS settings?
Clearing HSTS settings is generally unnecessary for regular users. However, if you encounter persistent issues accessing a website due to a privacy error or incorrect HSTS information, clear the HSTS settings and see if it helps.
Is HSTS Safe?
Yes, HSTS is safe and enhances web security by ensuring that communication with a website occurs over secure HTTPS. However, like any security measure, you should configure it correctly to avoid potential issues and other HTTPS errors.
Are There Any Downsides to Using HSTS?
If the site does not support HTTPS, HSTS can potentially lock out users from accessing a website if there are issues with the SSL/TLS certificate. Every website should enable HTTPS and adhere to the standard SEO and security practices.
Conclusion
Disabling HSTS settings in Chrome and Firefox is easy once you know the steps. Don’t let HSTS errors affect your browsing. With a few tweaks here and there, you’ll have the power to control HSTS settings and troubleshoot potential issues.
Now that you know how to disable HSTS in Chrome and Firefox, you should identify and resolve browser errors more efficiently. However, keep in mind that turning off security features should only be done as a last resort.
Save 10% on SSL Certificates when ordering today!
Fast issuance, strong encryption, 99.99% browser trust, dedicated support, and 25-day money-back guarantee. Coupon code: SAVE10

























