
You’re constantly under threat of cyber attacks, one of them being brute force attacks. They’re relentless, automated threats trying to crack your password by trying every possible combination. Fortunately, you’re not defenseless.
In this article, you’ll learn how to prevent brute force attacks and the steps you can take to identify and mitigate them. We’ll also introduce the best tools for penetration testing.
Let’s strengthen your defenses and shut the door on brute force attacks.
Table of Contents
Understanding Brute Force Attacks
A brute force attack is a type of cyber attack where hackers attempt to gain access to a system by trying all possible password combinations until they find one that works. It’s a simple, yet highly effective method if preventive measures aren’t in place.
Brute force attacks can be carried out manually or using automated software tools. The goal is to exploit weak passwords or password security mechanisms. In the case of online accounts, the attack involves repeatedly trying different combinations of usernames and passwords until the correct credentials are found.
There are several types of brute force attacks, such as:
- Simple brute force attack: This involves systematically trying every possible combination of characters until the correct password is found. It is time-consuming but can be effective if the password is weak or short.
- Dictionary attack: In this attack, hackers use a pre-defined list of commonly used passwords or words from a dictionary. The software automatically tries each word until it finds a match. This is more efficient than a simple brute force attack as it narrows down the possibilities.
- Hybrid brute force attacks: This combines elements of both brute force and dictionary attacks. It involves trying different variations of words, such as adding numbers or special characters to dictionary words.
- Reverse brute force attack: In a reverse brute force attack, hackers take a different approach by targeting a specific user or a small group of users instead of attempting to crack a single password. This method involves systematically testing a large number of commonly used or easily guessable passwords against a known username or a set of usernames.
Detecting Brute Force Attempts
In order to protect against brute force attacks, you need to be able to recognize the signs that one is happening.
- Monitor failed login attempts. The initial step to identify brute force attacks is to monitor failed login attempts closely. Numerous unsuccessful attempts from the same IP address or range of IP addresses are a clear indication of a possible brute force attack.
Note that these attacks often involve many IP addresses to disguise the actual attack source. Therefore, you’ll need to check for multiple IPs with excessive failed attempts. - Look out for unusual patterns, such as a high number of attempts in a short time or attempts during off-hours when users are less likely to be active.
- Spike in server load. Another crucial pointer is your server load. Brute force attacks can significantly increase server load due to the high volume of login attempts. If you notice a sudden, unexplained spike in server load, it could be a sign of an ongoing brute force attack.
- Geographical discrepancies: If you notice logins or login attempts from countries or regions where you don’t have users or where you don’t expect to see traffic from, it can be an indicator of a brute force attack.
- Multiple account access attempts: If one IP address is trying to access multiple accounts rather than just one, it can be indicative of an attacker trying to gain access to any account they can.
How to Prevent Brute Force Attacks
To effectively prevent brute force attacks, it is important to use a strong and varied strategy.
1. Adopt Strong Passwords
Start adopting strong passwords immediately to enhance your security. Strong passwords are your first line of defense against unauthorized access. Aim for password combinations that aren’t easily guessed – mix uppercase and lowercase letters, numbers, and special characters for complex passwords that are hard to crack.
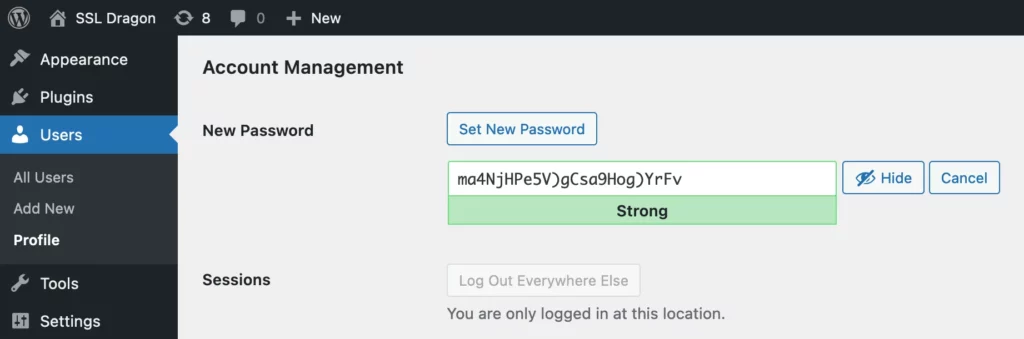
Never use birthdays, names, or common words. The more random and longer your password, the better. It might seem challenging to remember all these complex passwords, but that’s where a password manager comes in handy. It stores all your passwords securely and can help you generate strong, unique passwords too.
2. Limit IP-based Login Attempts
You’ll significantly increase your system’s security if you prohibit multiple login attempts from a single IP address, a technique known as IP blocking.
By limiting the number of failed login attempts from a specified IP address, you can be effective in brute force attack prevention. This strategy works by identifying unusual activity, such as a high number of failed login attempts in a short time frame, and then blocking the offending IP address.
It’s a critical component in preventing brute force attacks as it disables the attacker’s ability to try different password combinations. Keep in mind that the threshold for failed attempts should be reasonable to avoid blocking legitimate users.
Strengthen your defenses today by implementing IP blocking and keep your system safe from brute force threats.
3. Restrict Logins to Certain IPs
While it’s important to block suspicious IPs, it’s equally important that you restrict logins to certain trusted IP addresses to further strengthen your defense against brute force attacks.
By setting your system to only accept logins from predetermined IP addresses, you’re essentially creating a whitelist of trusted sources.
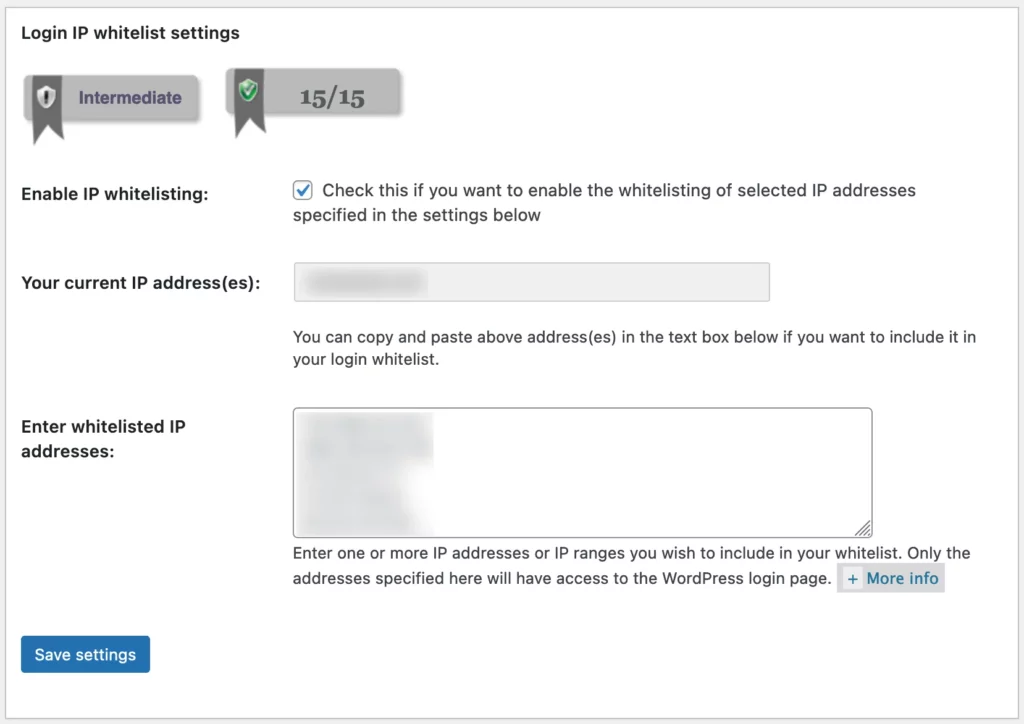
Should a login attempt be made from an IP address not on your whitelist, the system will immediately flag this as an unauthorized attempt and the login fails. This method of restricting logins to certain IPs greatly reduces the risk of brute force attacks.
However, to ensure optimal protection, regularly review and update your IP whitelist.
4. Implement Two-Factor Authentication
In addition to restricting logins to trusted IPs, you should also implement two-factor authentication to further strengthen your defenses against brute force attacks.
Two-factor authentication, also known as 2FA, is one of the most effective ways to prevent a brute force attack. It adds an extra layer of security to your authentication systems by requiring users to provide two forms of identification before accessing their user account.
This typically involves something they know, like a password, and something they have, such as a mobile device. When implemented correctly, 2FA makes it significantly harder for attackers to gain unauthorized access, even if they’ve somehow obtained your password.
5. Incorporate CAPTCHAs
Beyond implementing two-factor authentication, you can also incorporate CAPTCHAs for added security against brute force attacks. This step helps in brute force attack prevention by adding a layer of defense that computers find challenging to crack.
CAPTCHAs are designed to recognize human input, thereby helping to stop a brute force attack. They’re typically made of distorted text, images, or puzzles that are simple for humans but hard for bots to solve.
6. Use Specialized Login URLs
Switching to specialized login URLs is another preventive step you can take to discourage brute force attacks. They’re harder to guess, making them a valuable tool in your arsenal to block brute force attacks.
Don’t make it easy for attackers by using predictable login pages. Instead, create unique login URLs that aren’t easily discovered. The more complex the URL, the more difficult it’s for brute force software to find it.
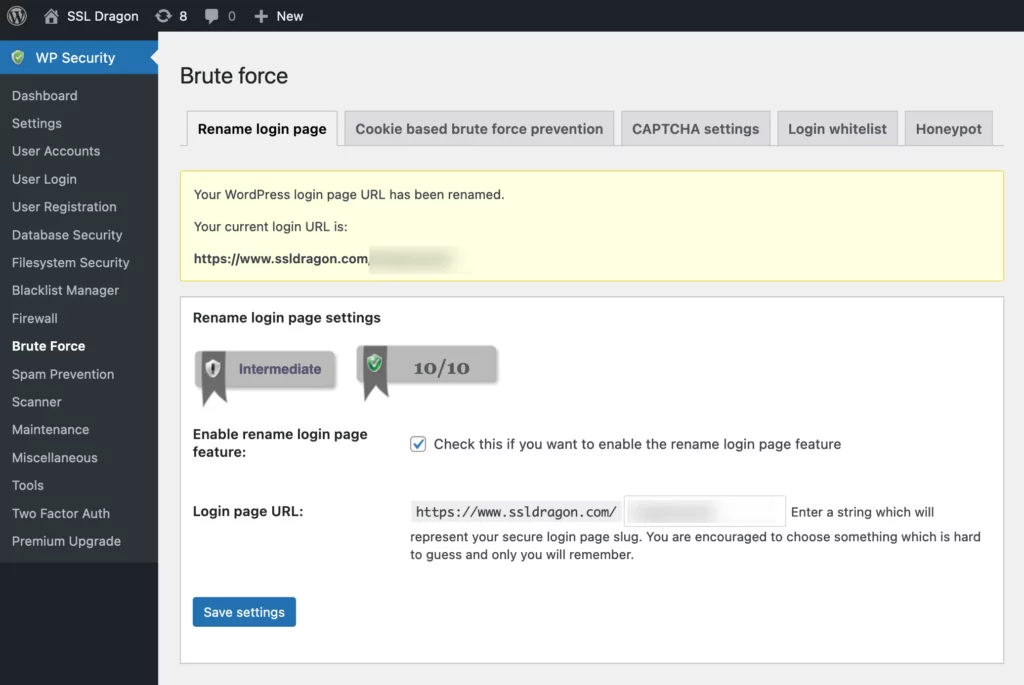
Remember, the goal is to make the hacker’s job as difficult as possible. By incorporating unique login URLs, you’re not only securing your login pages but also making a strong statement against brute force attacks. It’s a relatively simple change that can provide significant protection.
7. Deactivate Root SSH Access
Your server’s root SSH access is a prime target for brute force attacks, so it’s essential you deactivate it.
The secure shell, or SSH, allows the root user to log in and make changes to your server. However, this also leaves your system vulnerable to unauthorized users.
To deactivate root SSL access, navigate to your SSH configuration file. Find the line that says PermitRootLogin and change its value to no. This prevents the root account from logging in via SSH, effectively helping in brute force attack prevention.
Remember to save your changes and restart the SSH service for the changes to take effect. It’s a simple step, but it greatly enhances your server’s security.
8. Deploy Web Application Firewalls (WAFs)
In the battle against brute force attacks, you’ll find deploying Web Application Firewalls (WAFs) is an effective strategy.
A web application firewall serves as a protective shield between your system and the internet, filtering out security threats before they reach your servers. It specifically targets application layer threats, making it an essential tool to stop brute force attacks.
WAFs are capable of detecting and blocking suspicious activity such as repeated login attempts from the same IP address.
By employing a WAF, you’re adding an extra layer of security that can identify and counteract various forms of cyberattacks.
Tailor the rules and filters of your WAF according to your system’s needs, to enhance its effectiveness.
9. Set Progressive Lockout Delays
You can significantly boost your system’s security by implementing account lockouts with progressive delays after failed attempts, and this strategy effectively discourages brute force attacks.
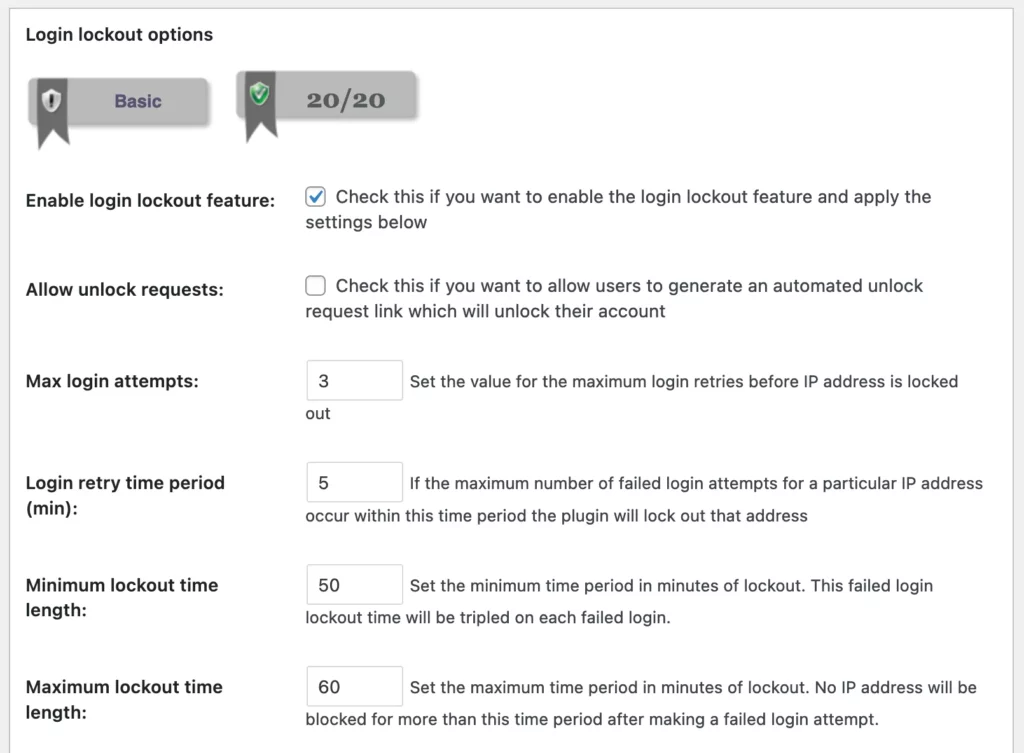
Using account lockouts means that after a predetermined number of failed attempts, the user’s account is temporarily disabled. This is where progressive delays come into play. Rather than locking the account for a fixed period, the lockout duration increases with each subsequent failed attempt.
This approach not only discourages hackers from making repeated attempts but also buys you precious time to detect and respond to the attack. It’s crucial, though, to strike a balance to avoid inconveniencing legitimate users.
10. Shift from Default SSH Port
By modifying the default SSH port, you’re making it harder for hackers to target your system. This simple change can greatly enhance your security against brute force attacks. When hackers attempt a breach, they often use brute force attack tools that target common ports like 22.
To modify the default SSH port, you’ll need to access your server’s SSH configuration file and enter a new port number of your choice. Ensure it’s a number above 1024 to avoid conflicts with other services. Afterward, restart your SSH service for changes to take effect.
11. Rename Admin Usernames
Renaming your admin usernames can add another layer of protection against brute force attacks. By doing this, you’re making it harder for attackers to guess your login credentials.
Admin is typically the default username, which attackers know and often try first to gain unauthorized access.
When you rename admin usernames to something less predictable, you reduce the chance of a successful brute force attack. Every failed login attempt is a win for your security. It’s not a foolproof method, but it’s an effective additional step.
Think about it: the harder your username is to guess, the longer it takes for an attacker to crack it. So, don’t make it easy for them.
12. Mandate Encrypted Connections
Ensuring your employees always connect through secure, encrypted channels is another key step in thwarting brute force attacks.
Secure, encrypted connections create a private network over a public one, ensuring that the data transmitted between your employees and your servers is encrypted. This encrypted data is unreadable to anyone who intercepts it, making it useless to potential attackers.
Enforcing the use of secured connections protects your sensitive data from being exposed and helps to maintain the trust of your legitimate users.
It’s critical to provide training to your employees on how to use these connections, as well as the importance of always using them for business-related communications.
No precaution is too small when it comes to preventing brute force attacks.
13. Promote Password Managers
You’re not alone in managing your passwords, and a password manager is a tool you can use to reinforce your defense against brute force attacks.
A password manager securely stores your login information, automatically fills in your credentials on websites, and generates strong, unique passwords. This tool eliminates the need to remember or repeatedly enter passwords, reducing the likelihood of employing weak passwords.
It also makes it more challenging for hackers to guess the correct password. Brute force attacks function by methodically checking all possible passwords until the right one is found. By using a password manager, you’re making this task exponentially harder for attackers, thereby significantly enhancing your cybersecurity.
14. Offer Cybersecurity Training
As part of your strategy to prevent brute force attacks, you’ll need to provide mandatory cyber awareness training to your team, and this will serve as a crucial line of defense. This training will equip your team with critical knowledge to understand the nature of cyber attacks and how to respond effectively.
It’s not enough to rely on technical safeguards; your team must be alert and prepared.
A comprehensive cyber awareness training program should cover the methods attackers use, including brute force attacks, and the signs to watch for. By making this training mandatory, you ensure that every team member is armed with the necessary knowledge to stop cyber threats.
15. Run Cybersecurity Simulations
Carry out cyber attack and phishing tests or simulations to enhance your defense against brute force attacks. This process mirrors real-life cyber attacks, allowing you to evaluate how well your system withstands incorrect password attempts, and how effectively your team responds to attempts at gaining access.
Simulations can help identify vulnerabilities, such as easily stolen credentials or weak points in your network. It’s important to test various attack scenarios, from simple incorrect password attempts to complex phishing schemes. The more you practice, the better prepared you’ll be to respond to actual threats.
FAQ
Do Hackers Still Use Brute Force?
Yes, hackers continue to use brute force attacks, especially when targeting weak or default passwords, as it’s a straightforward method to gain unauthorized access.
Do Firewalls Protect Against Brute Force Attacks?
Yes, firewalls, especially Web Application Firewalls (WAFs), can detect and block brute force attempts by limiting or blocking repetitive requests from the same IP address.
How Long Do Brute Force Attacks Take?
The duration of a brute force attack can vary widely based on the complexity of the password and the attacker’s resources. Simple passwords can be cracked in minutes, while complex ones can take years or even centuries with current technology.
What Is the Simplest Way to Stop Brute Force Cyber Attacks?
The simplest method is to enforce strong password policies and limit login attempts, effectively making brute force attacks impractical due to the time and resources required.
What Is the First Priority to Prevent Brute Force Attack?
The first priority is to use strong, unique passwords. Longer passwords with a combination of letters, numbers, and symbols significantly increase the time and effort required for a successful brute force attack.
Bottom Line
Protecting yourself from brute force attacks is crucial for maintaining security. By understanding what a brute force attack is, recognizing its signs, and implementing preventive measures, you’re taking a big step toward safeguarding your system.
Always stay alert – the digital landscape is constantly evolving, and with it, so are the threats. Don’t let your guard down.
Save 10% on SSL Certificates when ordering today!
Fast issuance, strong encryption, 99.99% browser trust, dedicated support, and 25-day money-back guarantee. Coupon code: SAVE10



























