
Navigating the world of internet security can be like trying to untangle a complex web. You’ve probably heard about the TLS handshake, a fundamental process that ensures a secure connection between a client and a server. But what happens during this intricate handshake process, and how do session keys, cryptographic algorithms, and the TLS version play a role?
In this guide, we’ll break down the protocols, processes, and encryption standards involved, helping you understand the nuances of the TLS handshake process.
Don’t let the jargon scare you! We’re here to make it all clear. And speaking of clarity, let’s start by answering the question: What is a TLS Handshake?
Table of Contents
- What Is a TLS Handshake?
- How Does TLS Handshake Work?
- TLS 1.2 vs TLS 1.3 Handshake
- Benefits of the TLS Handshake
- Limitations and Considerations
What Is a TLS Handshake?
The TLS Handshake, short for Transport Layer Security Handshake, serves as a protocol for initiating and establishing a secure connection between a client and a server, ensuring that the data exchanged between them remains confidential and tamper-proof.
It has its roots in the Secure Sockets Layer (SSL) protocol, which was its predecessor. As SSL evolved, it gave rise to TLS, addressing vulnerabilities and enhancing security. TLS is now the standard protocol for securing web traffic, emails, and data transmissions.
Both the client and the server play vital roles in establishing the encryption, where the client sends its capabilities, including supported TLS versions and cipher suites, and the server responds by selecting from these options.
How Does TLS Handshake Work?
While you navigate the Web, your browser engages in a complex process of negotiation and verification to establish a secure connection with the websites you load.
Let’s walk through the specifics of performing a TLS handshake, when it happens, what occurs during it, the detailed steps involved, and the possible SSL/TLS handshake failures you might encounter.
When Does a TLS Handshake Occur?
The TLS handshake takes place during the initial connection setup, securing interactions like a user accessing their online banking website. It ensures a secure channel between the client (user’s browser) and server (bank’s website) for protecting sensitive data throughout the session.
As the server sends its digital certificate for client verification, the client generates a premaster secret using the server’s public key, emphasizing the role of asymmetric encryption algorithms (private and public key pair) in this critical exchange.
The exact steps of the handshake process are designed to create a symmetric session key, establishing a shared secret for encrypted communication. Symmetric encryption algorithms come into play after the initial key exchange, securing the actual data transmission between the client and server.
In simpler terms, during the SSL/TLS handshake, the client and server exchange encrypted random byte strings. If the server requests a client certificate, the client responds by sending a random byte string encrypted with its private key, along with the actual certificate, or a signal indicating no certificate if it’s optional, forming a secure connection between them.
Here’s a simple breakdown of when a TLS handshake happens:
- When you access an HTTPS website (one with an SSL certificate) for the first time.
- During reconnection to a website after the session has timed out.
- When you initiate a secure transaction, like online banking or shopping.
- If you’re using a VPN, each time you connect.
- Whenever an application requires secure data transmission.
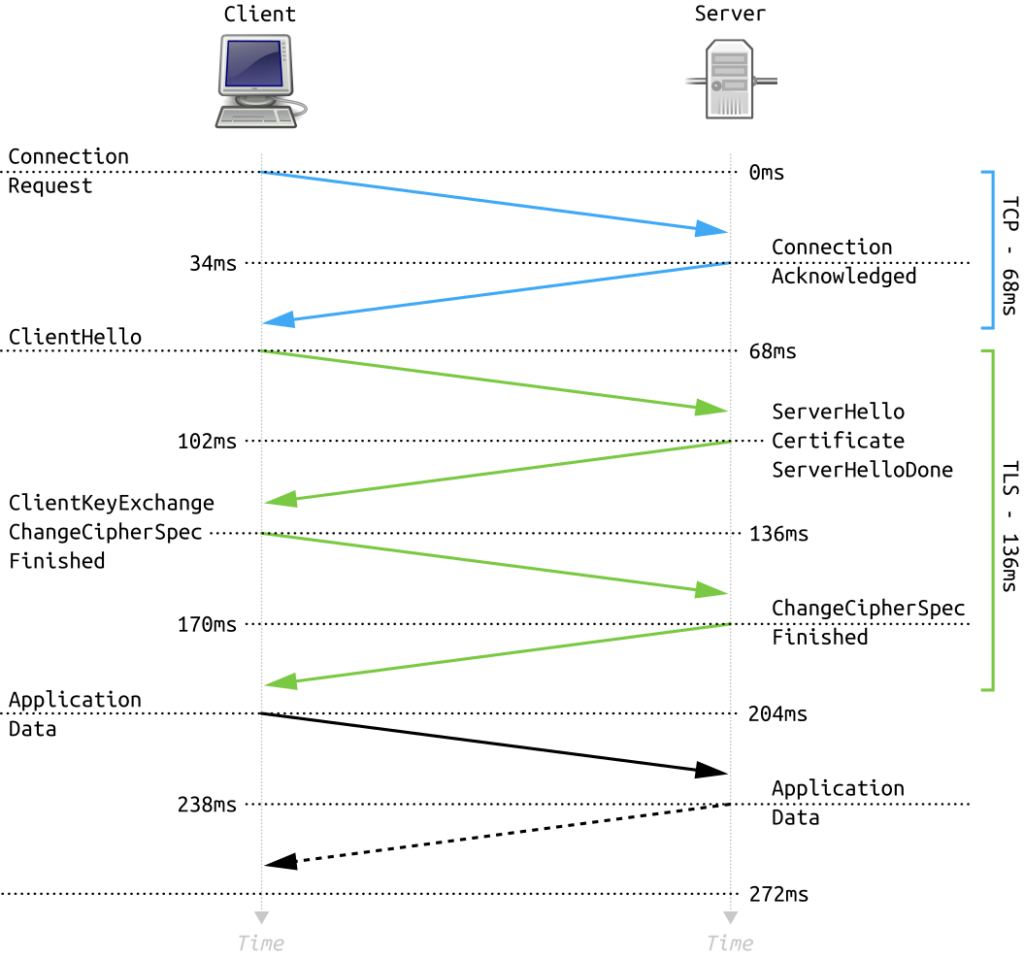
What Happens During a TLS Handshake?
Your browser first sends a ‘hello’ message to the server, outlining its capabilities, including the TLS versions and cipher suites it supports. The server responds with its own ‘hello’ message, selecting from the options provided.
A server certificate follows, which your browser validates to confirm the server’s identity. You then generate a pre master secret key, encrypt it with the server’s public key, and send it back. It’s a streamlined process designed for robust security and privacy.
The Steps of a TLS Handshake
Let’s break down the TLS handshake steps so you can better understand how this intricate process works. The specific steps in a TLS handshake vary based on the key exchange algorithm and supported cipher suites by both parties involved.
- Client Hello: The client sends a ‘Hello’ message with its SSL/TLS version, cipher suites, and a random byte string (Client Random).
- Server Hello: The server receives the message and responds with a ‘Hello’ message, its SSL/TLS version, selected cipher suite, and another random byte string (Server Random).
- Certificate Verification: The server sends its digital certificate for client verification.
- Premaster Secret: The client receives the cert, generates a premaster secret using the server’s public key, and sends it to the server. The server decrypts the premaster secret with its private key.
- Finished: Both parties compute a master secret and confirm the handshake’s completion.
Potential Failures in SSL/TLS Handshake
Having explored the steps of a TLS handshake, let’s now see why it sometimes can go wrong.
The first failure point can occur if the client can’t validate the server’s certificate, leading to an abortive handshake. It could be due to an expired certificate or a mismatch between the certificate’s domain name and the server’s.
Other common issues include incorrect implementation of the cryptographic algorithm or insufficient security measures, leading to breaches in data integrity.
Lastly, if the server doesn’t support the cipher suite proposed by the client, the handshake fails.
TLS 1.2 vs TLS 1.3 Handshake
TLS 1.2 is the predecessor of TLS 1.3, and the latter introduces several improvements over the former. Here are some key differences and improvements in the TLS 1.3 handshake compared to TLS 1.2:
Consider these fundamental differences:
- TLS 1.3 is faster. It reduces the handshake process from two round trips to just one, speeding up the connection time.
- TLS 1.3 removes outdated and insecure features. It eliminates obsolete cipher suites, offering a more secure connection.
- TLS 1.3 adds increased privacy. It encrypts more of the handshake process, minimizing the data available to potential eavesdroppers.
- TLS 1.3 simplifies the handshake. It defaults to a pre-shared key, streamlining the process.
- TLS 1.2 supports backward compatibility, while TLS 1.3 does not.
Upgrading to TLS 1.3 is recommended for improved security and performance in modern web applications and services.
Benefits of the TLS Handshake
You’ll experience numerous advantages when correctly implementing the TLS handshake in your online interactions. Most notably, the TLS handshake enables a robust level of security by establishing an encrypted connection between client and server. Encrypting messages via the use of SSL certificates is how we keep private info safe over the Internet.
The TLS handshake also supports a wide range of cryptographic algorithms, allowing you to adjust the balance between security and performance per your needs. You can use robust encryption algorithms to transmit sensitive data and faster, less taxing algorithms for less critical information.
Another significant benefit of the TLS handshake is its ability to authenticate the communicating parties. The server’s digital certificate, verified by a trusted Certificate Authority, ensures you’ll interact with the intended party, not an impostor. Additionally, client-side certificates can be used for mutual authentication, providing an extra layer of security.
Limitations and Considerations
The Transport Layer Security TLS protocol, though a powerful technology, isn’t perfect. Here are a few limitations and considerations to keep in mind:
- Performance Overhead: TLS handshakes can introduce latency, especially for short-lived connections. The initial handshake process is heavy and might affect the performance.
- Configuration Complexity: TLS settings and certificate management can be complex to configure correctly. Misconfigurations can lead to vulnerabilities.
- Version and Cipher Suite Compatibility: Not all clients and servers support the latest TLS versions or cipher suites. Compatibility issues can lead to handshake failures.
- Certificate Expiry: Certificates have a limited lifespan and require regular renewal. Failure to renew can result in connection errors.
- Vulnerability to Certain Attacks: Though TLS mitigates many security risks, it’s susceptible to man-in-the-middle or downgrade attacks.
Next, let’s answer the most frequently asked questions about the TLS handshake protocol.
FAQ
What Is the Difference Between SSL and TLS Handshake?
The SSL handshake is the predecessor to the TLS handshake. TLS (Transport Layer Security) is an updated and more secure version of SSL (Secure Sockets Layer).
Are TLS and TCP Handshake the Same?
TLS and TCP handshakes are not the same. The TCP (Transmission Control Protocol) handshake establishes a connection, while the TLS handshake occurs within the established TCP connection to secure the communication.
Is the TLS Handshake Encrypted?
Yes, the TLS handshake is encrypted. It establishes a secure communication channel by negotiating encryption parameters between the client and the web server.
Is TLS 1.1 Better Than TLS 1.2 Handshake?
No. TLS 1.2 is more secure than TLS 1.1 due to improvements in cryptographic algorithms and security features.
Is TLS 1.2 Better Than TLS 1.3 Handshake?
TLS 1.3 is more secure and efficient than TLS 1.2, with improvements in speed, encryption, and removal of obsolete features.
Is TLS 1.2 Outdated?
While TLS 1.2 is still widely used, it is considered less secure than TLS 1.3. Upgrading to TLS 1.3 (the latest protocol version) is recommended for better security.
Can TLS 1.2 and 1.3 Work Together?
Yes, TLS 1.2 and TLS 1.3 can work together, allowing for a gradual transition to the newer protocol while maintaining compatibility with older systems.
Conclusion
We’ve answered the What is a TLS handshake? question and went beyond to explain every intricate process behind it. Proper implementation is not merely a technical detail but a crucial step in protecting data transmitted from threats and unauthorized access.
While the TLS handshake’s steps may differ slightly between TLS 1.2 and 1.3, the core purpose remains the same. Despite some limitations, this process is undoubtedly at the core of sensitive web security and data protection.
Save 10% on SSL Certificates when ordering today!
Fast issuance, strong encryption, 99.99% browser trust, dedicated support, and 25-day money-back guarantee. Coupon code: SAVE10



























