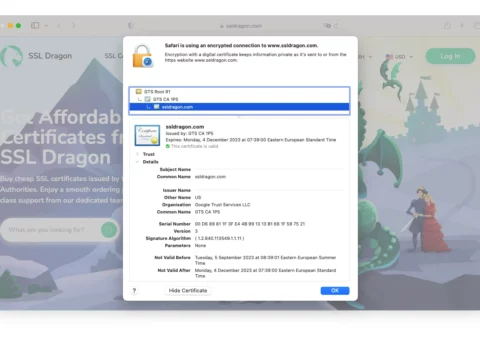
How to View the SSL Certificate of a Website
Do you want to make sure a website you’re visiting is secure? Knowing how to check the SSL certificate can help you determine if a website is trustworthy. In this article, we’ll guide you through the process of checking the SSL certificate of a website. By understanding the results, you’ll be able to confidently browse […]