If you manage a website or server, ensuring your SSL certificate is valid and properly configured is a top priority. One way to do this is with OpenSSL, a popular open-source cryptographic utility.
You can use OpenSSL to check the certificate expiration date, issuer, and subject. In this article, we’ll show you how to check a certificate with OpenSSL commands in Linux. Whether you are a web developer, system administrator, or just curious about SSL, this guide will provide the exact steps and command lines to check certificates with OpenSSL.
Table of Contents
- How to Check the OpenSSL Version?
- How to View the Full Certificate Details
- View the SSL Certificate Itself (Encoded)
- Check If the Key Matches the Certificate
- Check Who Issued the SSL Certificate
- Check Whom the SSL Certificate Is Issued To
- Check SSL Certificate Validity in Linux
- Display All the Above Info About the SSL Certificate
How to Check the OpenSSL Version?
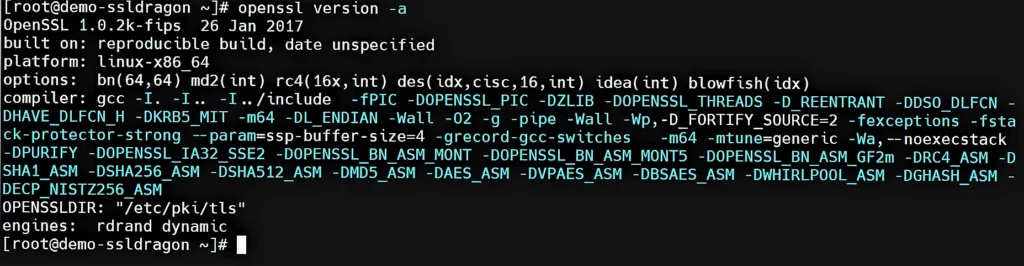
Most Linux systems will have OpenSSL pre-installed, but it’s better to ensure you have the latest running version. You can check your OpenSSL version by running the following command:
openssl version –a
Certificate files in Linux are located by default in the /etc/pki/tls/certs folder or sometimes within an application-specific folder such as /etc/httpd for Apache. These generally use .pem or .crt extensions and will likely be named yourdomain.pem or yourdomain.crt, but sometimes the generic “server” file name is used as well.
If you’ve applied for the SSL certificate and installed it on the server, you should already know its location and file names.
How to View the Full Certificate Details
You can use OpenSSL to check certificate validity, issuer, and subject separately or in one go. Ensure you have access to your server and SSH terminal.
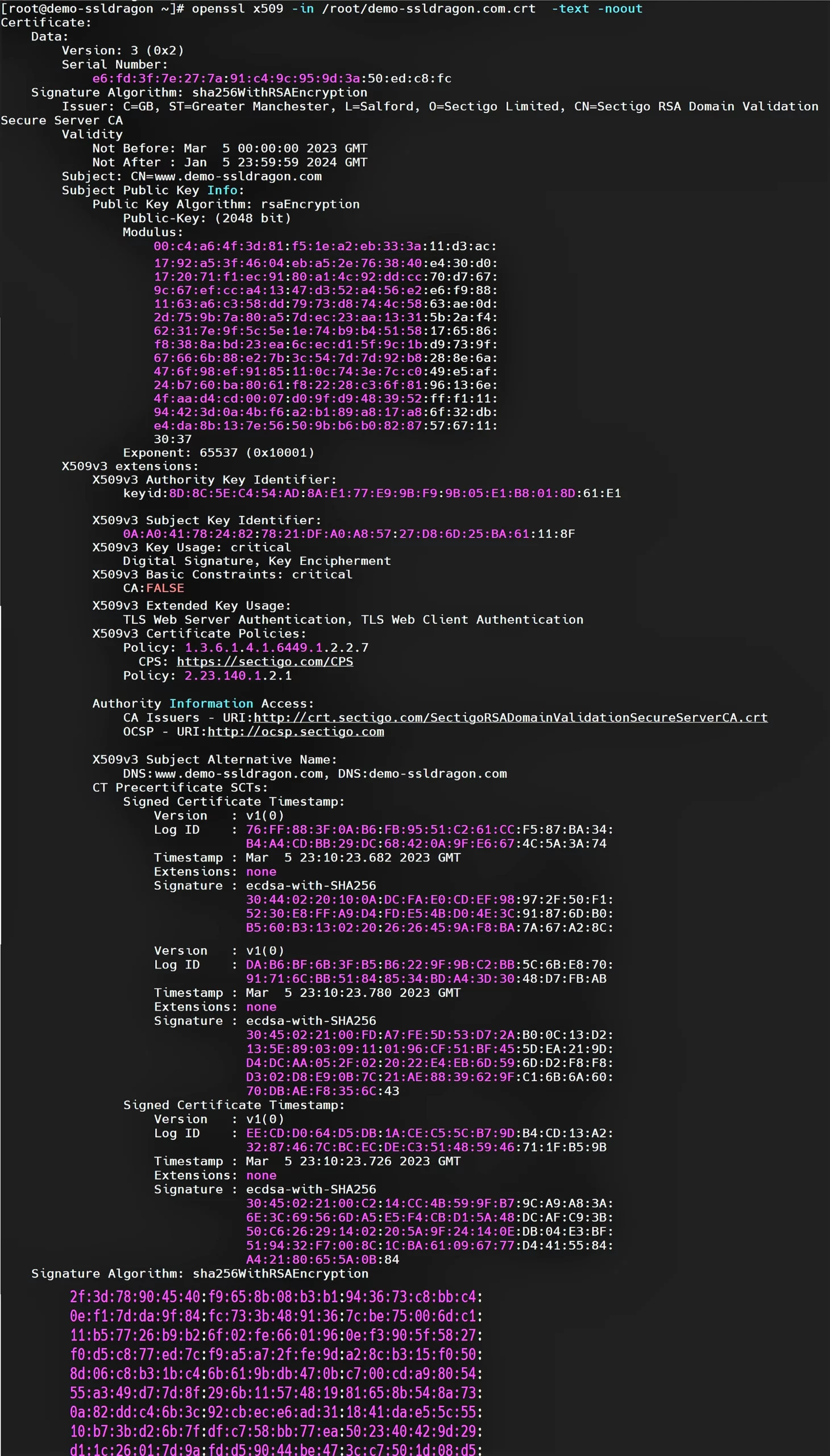
OpenSSL provides a rich variety of commands to generate, install, and manage certificates. To check the details of a particular certificate, run the following command:
openssl x509 -in /root/mycertificate.crt -text -noout
Use this OpenSSL command to check certificate expiry, subject, issuer, key details, and signature algorithm. Here’s what you should see:
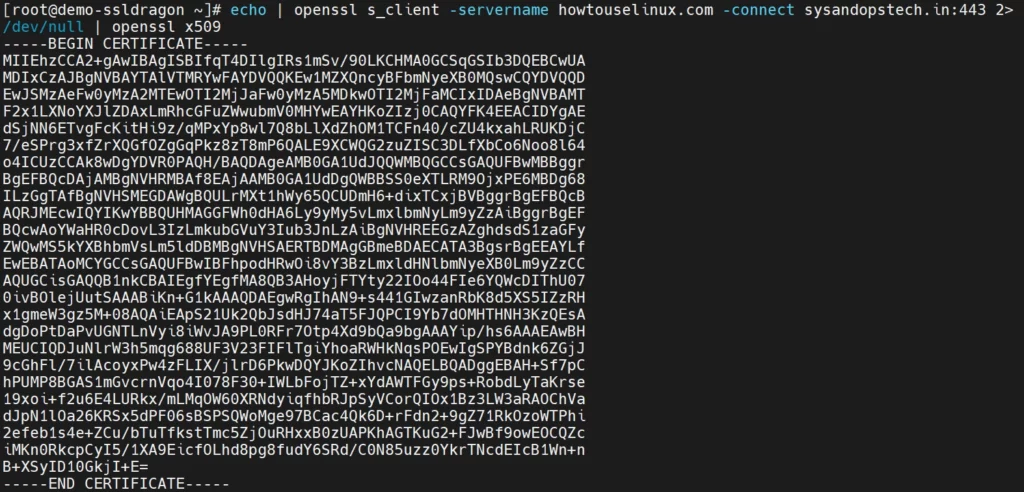
View the SSL Certificate Itself (Encoded)
OpenSSL allows you to view the SSL certificate in its original encoded format. Run the command below to display it:
$ echo | openssl s_client -servername howtouselinux.com -connect yourplc.com:443 2>/dev/null | openssl x509
Check If the Key Matches the Certificate
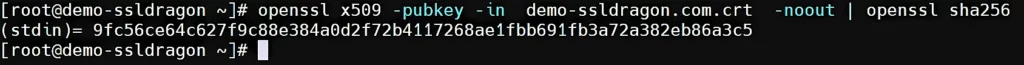
To verify if the public and private keys match, you need to extract the public key from each file and generate a hash output for it. All three files should share the same public key and the same hash value. Here’s how to use OpenSSL to check certificates and key details. The following commands to generate a hash of each file’s public key:
openssl pkey -pubout -in privateKey.key | openssl sha256
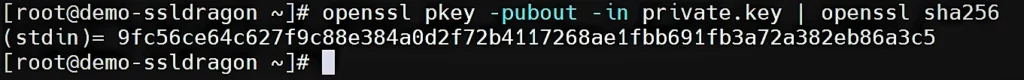
openssl req -pubkey -in CSR.csr -noout | openssl sha256
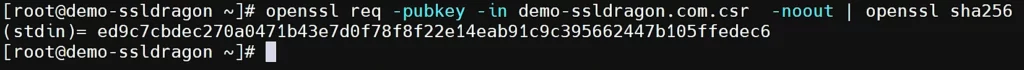
openssl x509 -pubkey -in certificate.crt -noout | openssl sha256
Check Who Issued the SSL Certificate
If you want to check the SSL certificate issuer, run the command line below. It will show you the Certificate Authority that signed the cert.
echo | openssl s_client -servername yourplc.com -connect yourplc.com:443 2>/dev/null | openssl x509 -noout -issuer
Check Whom the SSL Certificate Is Issued To
You can also check the subject of the SSL certificate. Depending on the validation type, you will see just the common name, or also the official company’s name.
$ echo | openssl s_client -servername .com -connect howtoyourplcuselinux.com:443 2>/dev/null | openssl x509 -noout -subject
Check SSL Certificate Validity in Linux
It’s important to know when the SSL certificate expires, so you can renew it in advance and avoid potential website outages and data breaches. Here’s how to check the SSL certificate expiration date in Linux:
$ echo | openssl s_client -servername howtouselinux.com -connect yourplc.com:443 2>/dev/null | openssl x509 -noout -dates
Display All the Above Info About the SSL Certificate
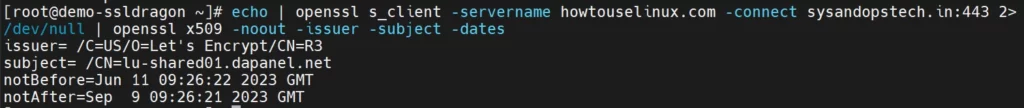
You can also use an OpenSSL command to check the certificate issuer, subject, and expiration date with the following command:
$ echo | openssl s_client -servername howtouselinux.com -connect yourplc.com:443 2>/dev/null | openssl x509 -noout -issuer -subject -dates
Final Words
If something goes wrong with your SSL connection, verifying your certificate’s details is the first step toward finding the culprit. In OpenSSL, you have a great utility to perform all kinds of checks, from inspecting the certificate issuer to analyzing technical data and seeing when the certificate expires. OpenSSL integrates with Linux and provides control over SSL installation via its flexible command lines.
Save 10% on SSL Certificates when ordering today!
Fast issuance, strong encryption, 99.99% browser trust, dedicated support, and 25-day money-back guarantee. Coupon code: SAVE10