
Understanding the SSL certificate chain of trust can be a bit of a struggle if you’re not familiar with the concept of Public Key Infrastructure.
You’re dealing with a series of digital certificates that each vouch for the authenticity of the previous one. It’s a rigorous hierarchy designed to ensure the integrity and security of data transfer between networks.
The chain starts with your browser trusting a root certificate, moving through intermediary certificates, and culminating at the server’s SSL certificate. And yet, there’s more to this cryptographic journey than meets the eye.
Let’s unlock this complex process together!
Table of Contents
- What Is the SSL Certificate Chain of Trust?
- Components of the SSL Certificate Chain of Trust
- How Does the SSL Certificate Chain of Trust Work?
- The Importance of the Certificate Chain of Trust
- SSL Certificate Chain Example
- Troubleshooting Chain of Trust Issues
What Is the SSL Certificate Chain of Trust?
The SSL certificate chain of trust is a sequence of certificates, each certifying the one before. It’s like a digital passport, ensuring that the data you’re sending and receiving is secure and from a reliable source. The chain of trust is a series of validations that the browser conducts to ensure the certificates are authentic.
When you visit a website, your browser will check if the site’s SSL certificate is valid. If it is, the browser will then validate the certificate’s chain of trust. This involves verifying the digital signature of each certificate in the chain, starting with the website’s certificate and ending with the trusted root certificate. If all certificates in the chain are validated successfully, your browser will trust the website and establish a secure connection.
Components of the SSL Certificate Chain of Trust
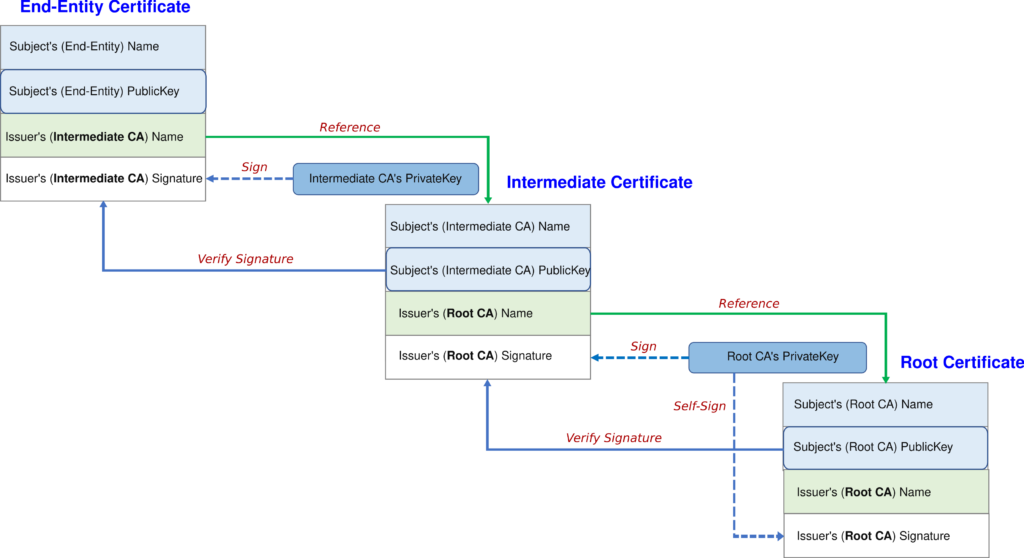
We’re about to explore the components of the SSL Certificate Chain of Trust: the Root Certificate Authority (Root CA), Intermediate Certificate Authority (Intermediate CA), and the Server (leaf) SSL Certificate.
Each plays a crucial role in establishing a secure, encrypted connection between a client and a server. Learning about their functions will help you see how trust and data security work on the Web.
Root Certificate Authority
The root certificate authority is the cornerstone of the SSL certificate system, serving as the highest level of trust in online security. Its primary role is to issue root certificates that validate the authenticity and security of websites.
By self-signing its certificate, the Root CA establishes the foundation of trust in the certificate hierarchy. These certificates are then utilized by intermediate certificate authorities to issue certificates to individual websites, forming the chain of trust.
Browsers rely on the Root CA to verify the legitimacy of websites through the issuance of trusted certificates. This process forms the basis of secure online communication and transactions.
Therefore, you should consider the varying levels of trust associated with different Root CAs. Some are more widely recognized and accepted, leading to more reliable certificate validation.
Intermediate Certificate Authority
One step below the Root CA in the chain of trust, there’s the Intermediate CA, which links the trusted root and the certificates issued to websites. As the name suggests, the Intermediate CA acts as a middleman, issuing intermediate certificates to branch out trust from the root to the endpoint websites.
The Intermediate CA decentralizes trust and enhances security, preventing the Root CA’s exposure. It signs certificates using its private key, which can be verified using its public key contained within the intermediate certificate. This signature establishes a chain of trust, extending from the root to the server via the intermediate certificate authority.
This hierarchy ensures that even if the private key of an Intermediate CA is compromised, the security of the entire chain remains intact, as the breach is contained within the intermediate level and does not affect the root certificates.
Server (Leaf) SSL Certificate
Following the chain of trust down from the Intermediate CA, we reach the Server SSL certificate, the final and most visible link in the certificate chain of trust. This cert, issued to the website owner, is the digital credential your browser checks when you visit a secure site. It’s proof of the server’s identity, ensuring you’re not connecting to an impostor site.
This Secure Sockets Layer certificate contains the server’s public key and details of the organization that owns the server, completing the chain of trust and tying it back to the Root CA through the Intermediate CA.
Moreover, server certificates also facilitate encrypted communication between your browser and the server, protecting sensitive information such as login credentials, credit card details, and personal data from interception by malicious third parties.
Websites with a valid SSL certificate are accessible on all browsers and systems and indexed in the search engine results pages.
How Does the SSL Certificate Chain of Trust Work?
Here’s a simplified step-by-step explanation of how the SSL certificate chain of trust works:
- You, the website owner, buy an SSL certificate: This server certificate authenticates your website’s identity and ensures secure data transmission.
- Certificate Authority (CA) issues your SSL certificate: They verify your request and provide you with the certificate. The CA is also trusted with a higher-level certificate from a Root CA.
- Root CA is pre-installed in web browsers: The Root CA is the top-level authority in the certificate chain of trust.
- Visitor accesses your secure site: Their browser initiates an SSL Handshake process.
- The browser verifies your SSL certificate: It checks the digital signatures of the issuing CAs, tracing the chain up to the trusted Root CA.
- Valid chain ensures secure connection: If all links in the chain are valid, the browser establishes a secure connection to your site.
The Importance of the Certificate Chain of Trust
Your sensitive information, such as credit card details or passwords, must remain secure in any online interaction. Here’s where the certificate chain of trust becomes essential. It verifies the authenticity of the website you’re visiting, confirming it’s not a fraudulent site. Without this verification, you’d be vulnerable to man-in-the-middle attacks, where a malicious entity could intercept and misuse your data.
Furthermore, the certificate chain of trust upholds the reputation of businesses online. If a website doesn’t use a valid SSL cert, web browsers will display security warnings to users. These warnings can deter potential customers and damage the company’s reputation.
In essence, the entire data security framework of the digital space hinges on the SSL chain of trust. It safeguards privacy and ensures the integrity of online transactions. Without this verification mechanism, the internet would be fraught with vulnerabilities, exposing users to risks.
SSL Certificate Chain Example
Here’s a simplified example of an SSL certificate chain. As a reference, we took PayPal’s SSL cert. You can inspect it yourself by going to PayPal’s website and clicking the icon next to the URL. In Chrome, select Connection is secure > Certificate is valid. A new window with the cert’s information will open. To see the chain of trust, go to the Details tab. Here’s what you’ll find there:
- Root Certificate Authority: DigiCert High Assurance EV Root CA
- Intermediate Certificate Authority: DigiCert SHA2 Extended Validation Server CA
- Server SSL certificate: www.paypal.com
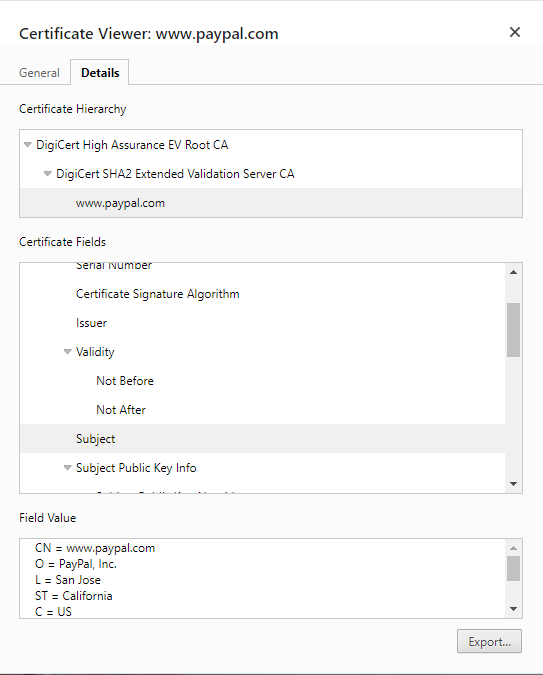
You can click on any certificate within the hierarchy and inspect the fields like Issuer, Subject, Validity, Signature Algorithm, Extensions, etc. Browsers publicly display all the certificate chains. You can use the same steps on most browsers and mobile devices for any domain.
Troubleshooting Chain of Trust Issues
Many connection errors stem from faulty SSL certificates, and the broken chain of trust is often the culprit. Below are the most common issues affecting it:
Expired SSL Certificates
When a certificate within the chain expires, it disrupts the trust between the server and the client’s browser. This is because browsers rely on the validity of each certificate in the chain to ensure secure connections. An expired certificate breaks this chain of trust, leading to security warnings or a failure to connect, as the browser cannot verify the authenticity of the expired certificate.
It undermines security by invalidating the trust between the server and the client’s browser. This lapse in validation poses a security risk, potentially exposing the connection to interception or data manipulation.
You can’t do much about the root and intermediate certificates, as only CAs can renew them. However, server SSL certificates expire every year and cause connection errors and website outages if you don’t renew them in advance.
Misconfigured Intermediate Certificates
Misconfigured intermediate certificates can disrupt the SSL chain of trust, creating security vulnerabilities and SSL errors. If not properly configured or installed in the correct order, the entire chain can be exposed, opening the door to potential cyber-attacks.
Knowing the correct installation order of intermediate certificates is a must, especially when, on some platforms, it differs. Generally, it starts with the root certificate, followed by intermediates, and then the end-entity certificate – just like the chain of trust. If you’re not sure about the order, read your server’s documentation about the intermediate root certificate and learn what is a CA-Bundle file.
One misstep in this sequence can break the chain, leaving users vulnerable to cyber threats. Each link in the chain must be up-to-date and properly configured to maintain a seamless and secure browsing experience.
Certificate Revocation List (CRL) and OCSP
Certificate Revocation List (CRL) and Online Certificate Status Protocol (OCSP) maintain the SSL chain of trust integrity. CRL contains revoked certificates, while OCSP provides real-time validation of certificate status. Together, they ensure that only valid certificates are trusted, strengthening the security of SSL/TLS connections.
However, reliance on CRL and OCSP introduces potential issues. CRLs can become large and cumbersome, leading to performance issues during retrieval and processing. Similarly, OCSP queries introduce additional latency as the client must communicate with the OCSP responder to validate certificate status in real-time.
Moreover, if the CRL or OCSP responder is unavailable or slow to respond, it can cause delays in establishing SSL connections or even result in false negatives where valid certificates are incorrectly flagged as revoked.
These issues highlight the importance of efficient management and availability of CRLs and OCSP responders to ensure smooth and secure operations.
Bottom Line
So, you’ve explored the complex nuances of the SSL certificate chain of trust. It relies on Publick Key Infrastructure and the security guidelines browsers and search engines refine regularly to keep the Web functioning.
If any link within the chain breaks, communication fails. Knowing this will help you fix any issues you may encounter. Remember, don’t use a self-signed certificate on a production website. Always get an SSL certificate from a trusted certificate authority.
Save 10% on SSL Certificates when ordering today!
Fast issuance, strong encryption, 99.99% browser trust, dedicated support, and 25-day money-back guarantee. Coupon code: SAVE10



























